Every one of us has probably gotten that reminder from your organization Help Desk telling you to please avoid clicking on phishing links in your emails. That is all well and good but URL’s are mysterious strings of characters which were written in an alien language that few understand. Below are a few things that are important to know if you want to learn some of the mysteries of the URL to help you from becoming a victim of online phishing or malware.
How to quickly spot a phishing email (hover your cursor over ALL links)
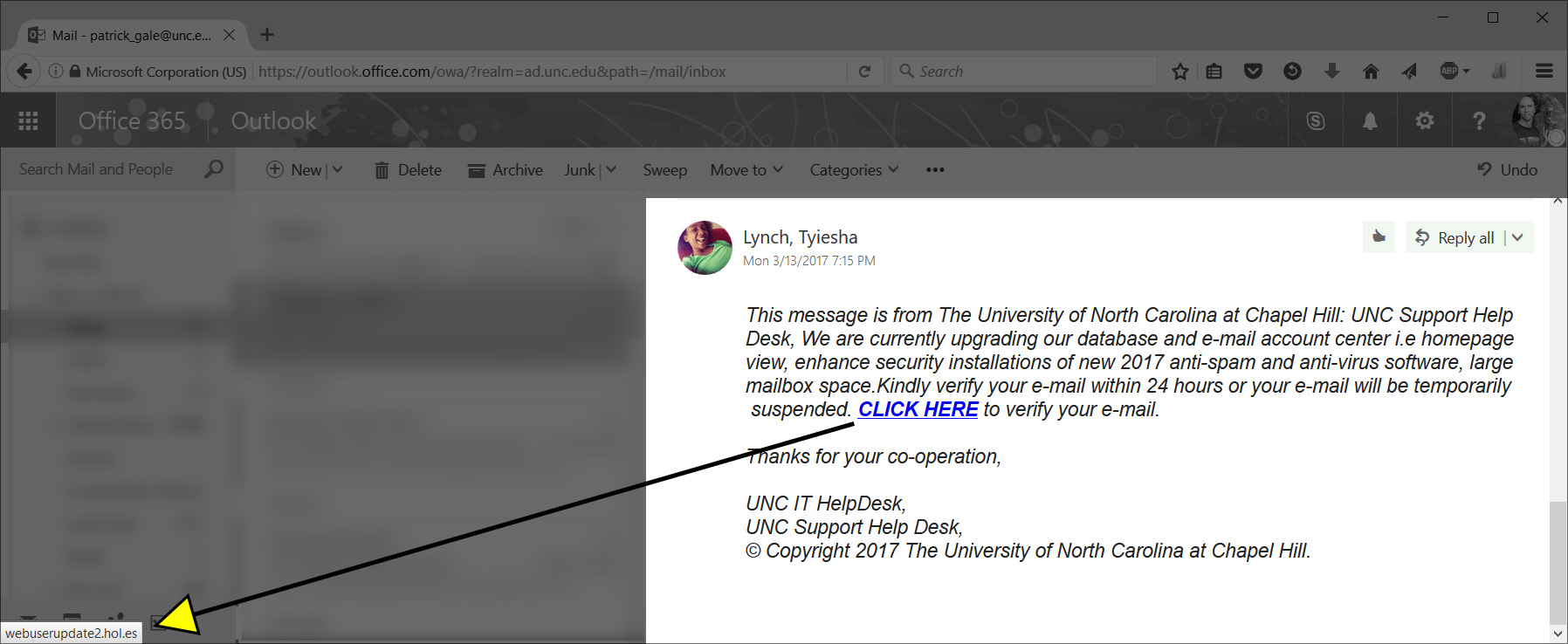
Just a quick tip on spotting phishing emails. Before clicking on ANY link in an email (or website), place your cursor over the link and look at the web address for the link that appears in the lower left-hand corner of the window (shown in the image below). For instance if you hover over this link you should see http://unc.edu (or simply unc.edu). Phishing emails are usually reported to campus ITS before they even reach your email box so you can always check to see if a suspicious email has been reported by going to http://its.unc.edu/phish-alerts/ (again hover over this link to see where it is going before clicking on it).
Don’t trust online URL scam checker sites
To begin, there are no good sites out there for checking a URL (web address or website) to determine if it may be a phishing or malware site. A recent URL sent through email as a phishing attempt is a case in point (http…://connectcarolina.c0.pl/sso.unc.edu/idp/Authn/UserPassword/…). I changed the URL to keep you from clicking on it by adding … to it, so you are safe. Anyway, if you pasted the URL (without the …) into a service such as scanurl.net, safeweb.norton.com, or urlvoid.com (to name a few) it would probably say the site was safe. Don’t believe them.
First of all, none of these ‘verifier’ sites build in enough artificial intelligence to effectively read the website content and code to determine the ‘intent’ of a page. I tried several of these services and it said the content came from an education website and was minimal risk (only because the content of the page had references to UNC and probably links back to UNC websites). Minimal risk means nothing here.
Who and what do you trust?
Well for starters, you can not always trust the sender. Someone sending phishing emails can easily write a program that will send you an email that looks like it is coming from any legit email address (like your mom or your organizational help desk). It is not difficult at all.
The most useful thing to know is how to read and recognize the domain/website the URL is referring to (Google ‘How to Read a Web Address‘ for additional reading). In the URL above we are only interested in the domain which is made up of the name of the domain ‘c0’ and the extension of the domain ‘.pl’. The ‘connectcarolina’ and ‘sso.unc.edu/idp/Authn/UserPassword’ parts of the URL can simply be thought of as folders within the c0.pl website. The domain is always the last two strings joined by a period between the http:// part and the first / in the URL. So in the URL http://pgale.web.unc.edu/homepage, the domain is simply unc.edu (again the last period joining two strings before the first /).
Now that we can recognize the domain name in a URL, things are a bit easier. An educational domain (like unc.edu) or reputable company domain (like google.com) most likely will impose harsh penalties for posting malicious webpages on their websites or have restrictions to help prevent it, and probably any domain hosted in the USA. If you Google the domain ‘c0.pl’ you will see that the domain service is for ‘CBA.PL – Najlepszy i najpopularniejszy darmowy hosting’. I have no idea what ‘Najlepszy i najpopularniejszy darmowy’ means. If you can’t recognize the domain then that is a red flag to avoid the site.
To complicate things
Some things to watch out for are, first, your email client/program. If you use OWA (Outlook Web App.) for instance, then it may be using URL rewriting to make all the links in your emails read as https://outlook.unc.edu/owa/redir.aspx?SURL=… (with a lot of jibberish at the end). This is a problem because it invalidates what I just mentioned above about trusting the domain of the URL. In this case it looks like the URL domain is unc.edu right? Well it is, however that is simply the starting point.
This brings me redirects. Most of you may be aware of URL link shortener services. Here at UNC there is the service http://go.unc.edu/. So if I wanted to create a URL redirect to my website with a shorter URL it may look like http://go.unc.edu/r3BFg which redirects you to ‘https://pgale.web.unc.edu/’. Do you see the problem here? You don’t know what the final destination of the URL is! At this point an online tool that checks your links to show you the final destination is helpful, such as http://www.internetofficer.com/seo-tool/redirect-check/. If you copy http://go.unc.edu/r3BFg and paste it into the URL checker it will show you the URL is redirected to https://pgale.web.unc.edu/. I would trust that site (since it is mine).
Other tools to help if you happen to go to a malware site
So say you learned all of the tricks above but still ended up a malicious website by mistake. One way to protect yourself even if you do end up on a malicious website (through a website search or email link) is to use a script blocking tool. Scripts are things on websites for displaying content (videos and images), but also adding bad things to your computer in some cases. If you use the Firefox browser, a tool of choice for me is NoScript (https://addons.mozilla.org/en-US/firefox/addon/noscript/). Now I realize most people would lose their patience with this plugin since it forces you to verify domains you trust, but it is worth learning. Even if I were to browse to a website with malicious software embedded in it, it is highly unlikely I would get infected. I would be able to leave the site before it caused harm to my computer since I can choose the sites I will accept scripts from (for displaying everything from videos to images). There are similar tools for other browsers such as Chrome, but I’m a Firefox kind of guy myself. At any rate, I feel NoScript is one of the most useful tools for helping to prevent you from bad websites online.
I will leave it at that. There is enough on this page to make your head explode I know, but hopefully you were able to learn something from my experiences.


 pgale scripting library hosted by UNC Source Control (Git)
pgale scripting library hosted by UNC Source Control (Git) Add contact info to your phone lock screen
Add contact info to your phone lock screen How To Improve Your WiFi Service
How To Improve Your WiFi Service